1. Introduction
There can only ever be one program or service using a certain port at a given moment. There are instances when discovering what process using a certain port is necessary. In this guide, we will examine several methods for determining which processes using a port on Linux.
2. The Root’s Permission
In Linux, the process’s full details are only accessible to the system administrator or the owner of the process.
We can’t tell whose process it is when we want to see whether it’s listening on a certain port.
Given root access, we can learn anything we need about the process, including its unique identification.
As a result, it’s possible that we’ll have to run our network services as the root user (or with sudo).
3.1. netstat tool for Processes Using a Port on Linux
The netstat utility is part of the larger net-tools suite.
It used to be standard fare on many Linux systems. On the other hand, the net-tools package hasn’t been updated since 2011.
The net-tools package is no longer up to date since it does not support the features of the current Linux kernel, among other reasons.
But netstat is still popular, so let’s see how it actually helps us:
sudo netstat -ltnup
A sample of the netstat command’s output is shown below.

In the preceding example, we used the parameters ltnup with netstat to see all open ports.
Consider the meanings of the flags used here:
The l option will only display the sockets that are actively listening.
To see TCP connections, type t.
n – numerically display addresses
to display UDP connections
p – display current process/application name
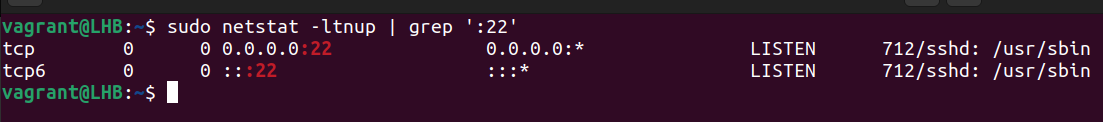
We can find the PID and Process name of the listening process for a certain port in the final column of the report we just saw above.
To retrieve detailed information about a specific port’s processes, we can simply feed the netstat output into the grep tool and filter the results.
Check out which program is listening on port 22 as an example:
sudo netstat -ltnup | grep ':22'
3.2. SS Command for Processes Using a Port on Linux
The net-tools package that was mentioned in the preceding section is no longer supported.
ss now serves as the new netstat command.
Let’s have a look at using the ss command to see which process is using port 22:
ss -ltnup 'sport = :22'
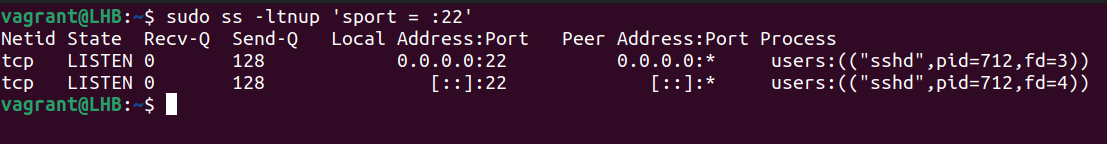
The parameters we supplied to the ss command are identical to the ones we supplied to the netstat command.
The only difference was that, rather than running a second grep process, we filtered the output using the ss utility’s state filter.
In the same way that the netstat command’s output has process information in its final column, this is also the case.
3.3. Use of the lsof Command
In Linux, you may see a list of currently open files using the lsof command.
Applying the lsof command with the -i:port number option allows us to identify which process is connected to a certain port:
sudo lsof -i :22
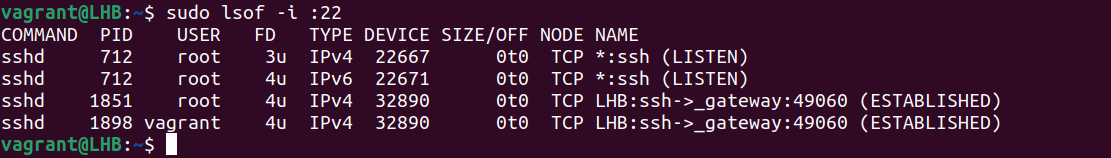
The name of the process that is listening on port 22, together with its process identifier (PID), owner, and file descriptor, are shown in the first four columns of the output above.
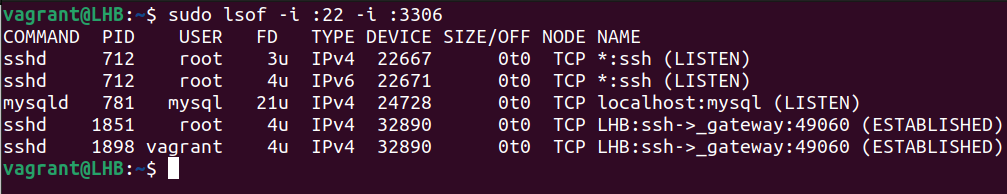
To see which programs are listening on which ports, we may use the lsof command with multiple -i:port arguments:
sudo lsof -i :22 -i :3306
3.4. the fuser Command for Processes Using a Port on Linux
This tool, called fuser, shows which programs are using certain sockets, named files, and file systems. Many recent Linux versions have it preloaded by default since it is part of the psmisc package.
In this way, we may examine data on a certain port’s active process. To repeat, let’s discover the PID of the process that is listening on TCP port 80:
sudo fuser 80/tcp
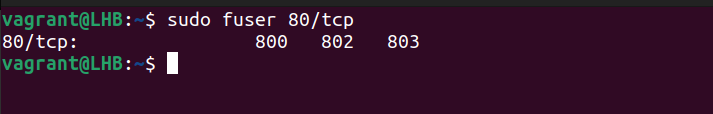
The above result is rather simple to understand. The PID 800, 802, 803 processes is currently listening on TCP port 80.
Unfortunately, it provides just a general overview of the procedure without any specifics; for instance, what is the actual name of Procedure 800? Who is responsible for this procedure? as well as the others.
The fuser command’s “-v” option enables verbose output, which is useful if we want to learn every nuance of the procedure:
sudo fuser 80/tcp -v

The fuser command allows us to simultaneously examine the state of many TCP and UDP ports:
4. Concluding Up
To summarize, this brief article introduced four alternative Linux command-line tools with examples for determining the details of the process listening on a certain port.
Each of these commands is a potent source in our Linux journey.
